Patterns in Cyberspace using DMARC
I recently read Peter Hansteen’s Predicting developments in real world conflict from patterns of failed logins which got me thinking about some of the systems I administer.
DMARC and Spam
I decided to take a look at DMARC patterns since at work I had set up a Grafana console and a really useful utility called Parsedmarc which would grab emails from an IMAP server and parse them and add them to the data.
I found some interesting things. First, traffic from Ukraine had gone up and it had spiked sometime on the 13-14th February 2022. There were some smaller spikes on the 19th-20th and again on the 28th, but that first spike was interesting. My company’s domain received reports of 38 spoofed emails.
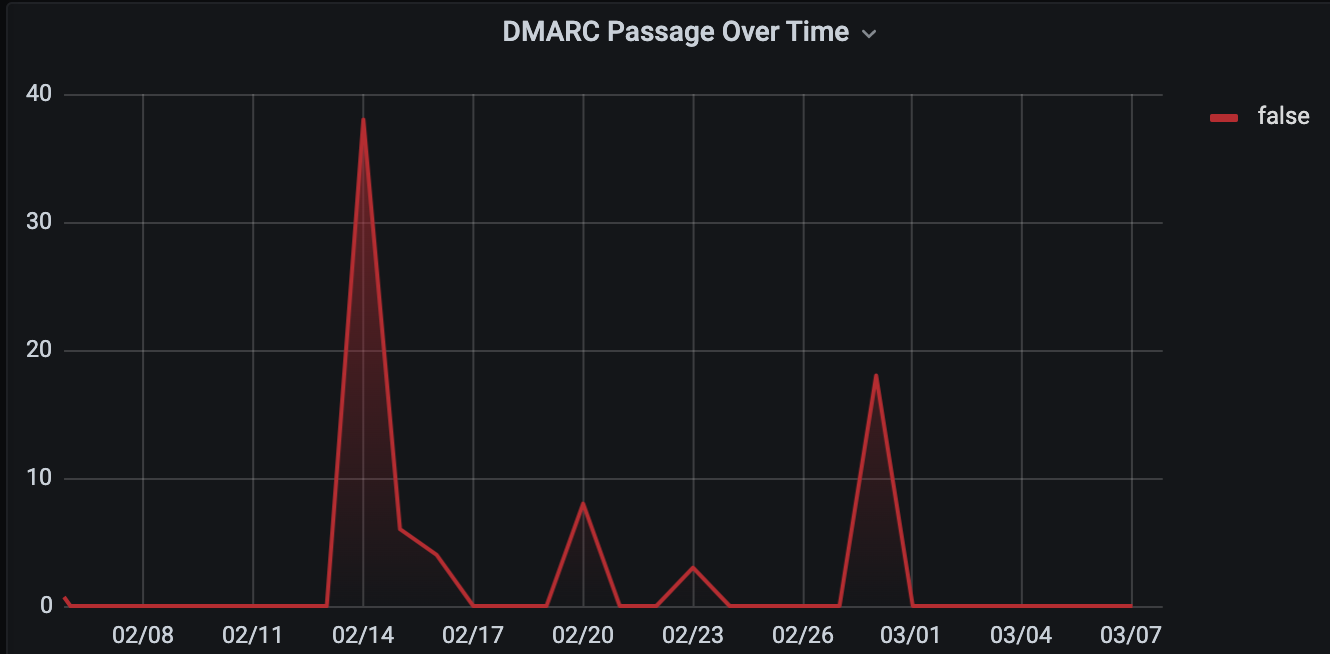
In the past 30 days, we received a total of 81 reports from Ukrainian IP addresses attempting to spoof email with domain.
There were a total of 5 IP addresses. One of them was using a reverse DNS domain of a website of a horse ranch in the United States, but WHOIS clearly identified the IP as belonging to a block in Ukraine.
The other reverse DNS hostnames corresponded with various Ukranian looking domains (one of them had ‘kyiv’ in it and another ended in .ua)
This may not look like a lot of data, after all we probably don’t get the sheer amount of data other sites do, but it is definitely interesting to say the least.
I think I’ll keep my eye on DMARC and see what other patterns pop up.
